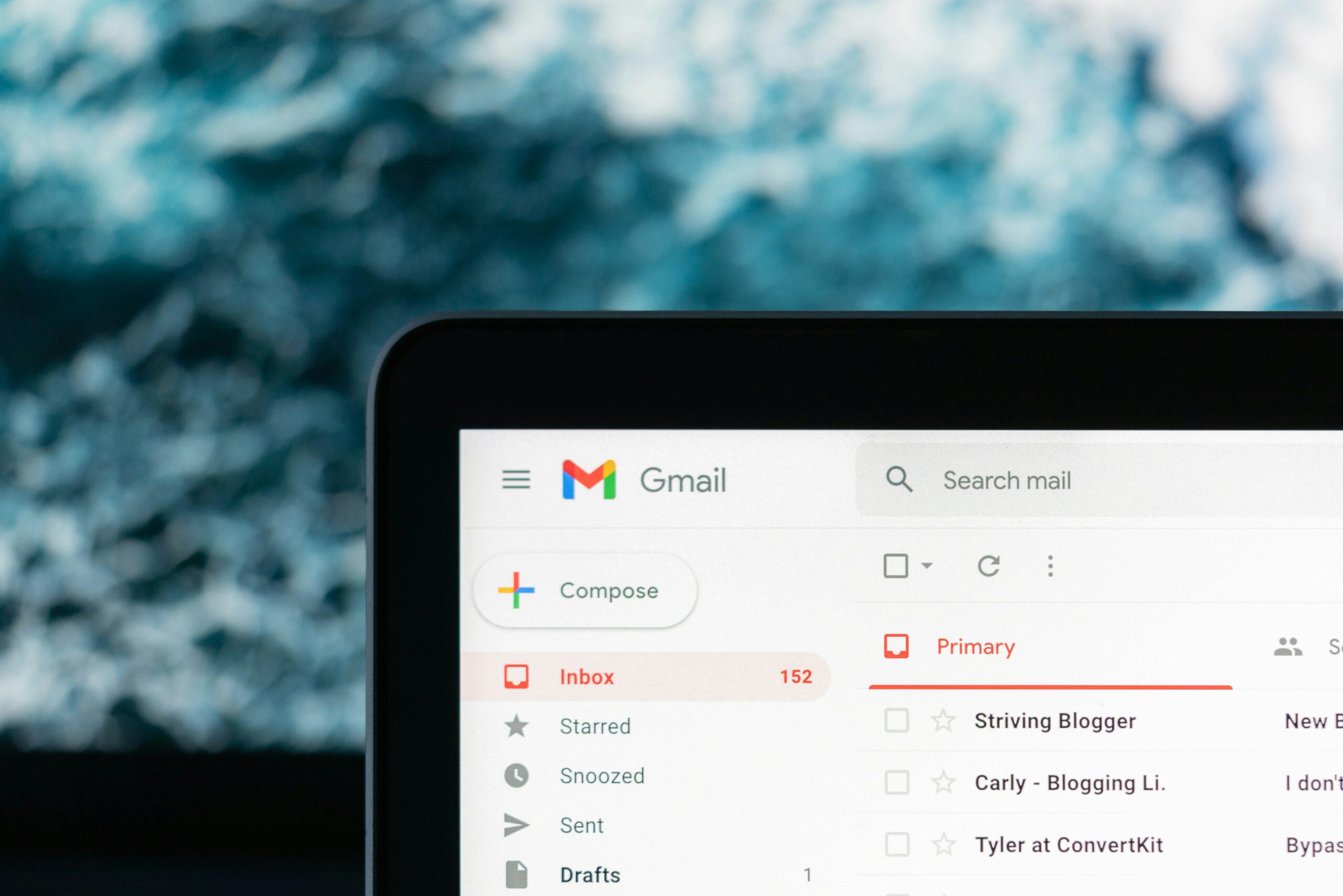
Introduction to Authy and Its Purpose
Authy is a robust two-factor authentication (2FA) application designed to enhance online security by providing an additional layer of protection for user accounts. The application generates time-based one-time passwords (TOTPs), which are essential for ensuring that a user’s identity is verified before accessing sensitive data or services. By requiring both a password and a TOTP, Authy significantly reduces the risk of unauthorized access, thereby safeguarding personal and financial information from potential cyber threats.
Available across multiple platforms, Authy was initially launched for mobile devices but soon expanded to incorporate desktop applications, making it even more accessible for users. Designed to be compatible with both iOS and Android operating systems, the mobile app enabled users to manage their 2FA needs conveniently from their hand-held devices. The desktop app facilitated an alternative method for users who preferred to access their security tokens from their computers, enhancing usability in various environments—be it at home or in an office setting.
As online security increasingly becomes a priority for individuals and organizations alike, tools like Authy play a critical role in mitigating risks associated with data breaches and identity theft. The application not only generates the requisite codes needed for login but also provides features such as multi-device synchronization and backup recovery options, further bolstering its functionality. However, recent developments indicate a transition toward a mobile-only approach, suggesting that users will need to adapt to relying primarily on the mobile app to ensure continued access to their authentication tokens. This shift highlights the evolving landscape of digital security tools and the importance of staying abreast of technological changes.
Recent Announcements: What We Know
Recently, Authy announced the discontinuation of its desktop application, a significant shift in its operational strategy. This decision arises from an evaluation of user engagement and the growing trend toward mobile-centric solutions for two-factor authentication (2FA). According to recent statistics, the desktop app has seen a decline in user activity, with less than 10% of Authy users opting to utilize the application for their authentication needs. In contrast, the mobile app has gained immense traction, accounting for the majority of daily authentications.
The feedback from the community, gathered through surveys and forums, highlighted the preference for mobile devices as the primary method for managing 2FA. Users indicated a desire for a more streamlined experience that aligns with their increasingly mobile lifestyles. This feedback was pivotal in guiding the company’s decision to focus its resources on enhancing the mobile application experience, which offers improved functionality and convenience for its users.
In an official statement, Authy developers emphasized their commitment to delivering a robust mobile application that meets evolving user expectations. They noted that the desktop app’s discontinuation would allow the company to allocate its development efforts towards expanding features and optimizing security measures within the mobile platform. This transition reflects broader industry trends towards mobile authentication solutions that offer greater accessibility and reliability.
As part of this transition, users of the desktop app are encouraged to migrate to the mobile version, which provides a comprehensive array of features that enhance user security. Authy’s team has assured users that they will continue to support the mobile application with regular updates, ensuring that users have access to the latest in security technology.
The Shift Towards Mobile-Only Authentication
In recent years, there has been a notable shift in the way users authenticate their digital identities, moving increasingly towards mobile-only solutions. This transition has been influenced by several factors, including the widespread adoption of smartphones, advancements in mobile technology, and changing user preferences. Mobile authentication apps offer unprecedented convenience and security, appealing to both individual users and organizations alike.
One of the primary drivers of this trend is the growing reliance on mobile devices for daily tasks, including banking, shopping, and communication. As more individuals prefer using their smartphones for these activities, the demand for mobile authentication tools has surged. Mobile apps, such as those providing two-factor authentication (2FA), allow for quick access and rapid response to security needs, making them an integral part of the user experience. The convenience of accessing authentication tools directly from a mobile device far surpasses traditional desktop applications.
Moreover, mobile authentication apps tend to have enhanced security features compared to desktop counterparts. They often incorporate biometric security measures, such as fingerprint recognition or facial recognition, which are not available on most desktop platforms. These features help mitigate unauthorized access and enhance user confidence. As mobile phones are constantly evolving, they are becoming more capable of supporting sophisticated security protocols, thus reinforcing the case for a mobile-only approach.
This shift also aligns with the evolving digital landscape, where cloud-based solutions and on-the-go connectivity are paramount. As organizations continue to embrace digital transformation, the need for versatile security solutions becomes essential. Mobile authentication not only meets this demand but also fosters a seamless user experience, encouraging users to adopt secure practices in their digital interactions. Consequently, the discontinuation of desktop applications like Authy appears to be a strategic move towards embracing the future of security technology.
Impact on Users: Transitioning from Desktop to Mobile
The discontinuation of the Authy desktop app marks a significant shift for users who have relied on its features for managing their two-factor authentication needs. As the focus moves towards a mobile-only platform, existing users will need to navigate this change effectively. Transitioning from the desktop app to mobile is not merely about changing devices; it also encompasses transferring data and adapting to a new workflow.
First and foremost, users should begin the migration process by installing the Authy mobile app on their smartphones. The application is available for both iOS and Android devices, allowing users to choose their preferred platform. Following installation, users can log in using their existing Authy account credentials. The authentication process is straightforward—upon entering the phone number linked to the account, users will receive a one-time password (OTP) to verify their identity.
Data migration is a critical step, and Authy facilitates this by automatically syncing a user’s account details once they log in on the mobile app. Users are advised to ensure that they have received their authentication tokens on the mobile device before uninstalling the desktop app. While the transition is designed to be smooth, some users may encounter challenges such as lost tokens or difficulties with account verification. To mitigate these risks, keeping a backup of the recovery codes provided during the setup process is crucial.
Additionally, users should take time to familiarize themselves with the mobile interface, which may differ from what they have previously used on the desktop. Engaging with online resources and tutorials can significantly help in easing the adjustment period. By adopting these recommendations and being proactive about the transition, users can successfully adapt to a mobile-only future while maintaining access to their two-factor authentication features.
Mobile vs. Desktop: A Comparison of Usability
The rise of mobile applications has significantly reshaped how users interact with digital services, particularly regarding security protocols like two-factor authentication (2FA). When comparing mobile and desktop applications, usability emerges as a critical factor that influences user preference and overall experience.
Mobile applications, with their inherent design for touch interfaces, tend to offer more intuitive user experiences. Many users find it easier to authenticate identity via their smartphones, which seamlessly integrate biometric features such as fingerprint scanning and facial recognition. These functionalities not only enhance security but also streamline the authentication process, making it quick and user-friendly. Conversely, desktop applications often rely on traditional input methods, such as typing passwords and codes, which may slow down verification efforts due to the need for additional hardware like keyboards and mice.
Convenience is another significant advantage of mobile apps in the realm of two-factor authentication. Users can generate authentication codes or approve login requests directly from their smartphones, which are typically always within reach. This accessibility is especially beneficial when users are on the go. In contrast, desktop applications may restrict users to specific environments, hindering their ability to authenticate themselves swiftly. The need to switch devices can create unnecessary barriers, thereby affecting user satisfaction.
Moreover, security features are critical when assessing usability. Mobile applications often leverage secure elements built into smartphones to store authentication data safely, thus minimizing the risk of unauthorized access. Many of these applications also provide options for cloud backups, ensuring that recovery is both possible and convenient. In contrast, desktop applications may not offer the same level of security directly tied to device-specific features. As a result, users may feel more secure using mobile solutions for their two-factor authentication needs.
Both usability and security are paramount in the context of two-factor authentication, and mobile applications are increasingly becoming the preferred choice for users seeking effective, convenient, and secure authentication methods. The discontinuation of the Authy desktop app highlights this shift towards a more mobile-centric future in data protection strategies.
Alternatives to Authy Desktop: What Are Your Options?
As the Authy desktop app is being discontinued, users seeking alternatives can explore several desktop-based authentication solutions that cater to various needs. One popular option is the Microsoft Authenticator. Although it primarily targets mobile users, Microsoft offers a web version allowing desktop access. Its integration with Microsoft accounts presents a seamless experience for those embedded in the Microsoft ecosystem. However, users utilizing non-Microsoft accounts may find it less flexible.
Another noteworthy option is Google Authenticator. Like Microsoft Authenticator, it is primarily a mobile app but supports QR code scanning on desktop for logging into accounts. This tool is straightforward, featuring a simple interface. While both options allow for two-factor authentication, neither has a dedicated desktop application, which might limit versatility for some users.
For those willing to invest in a robust solution, Duo Security is an excellent alternative. Primarily used by enterprises, Duo provides a comprehensive identity verification platform. With desktop authentication features and a mobile app, it offers a range of integrations and advanced security options. On the downside, the complexity might be overwhelming for personal users or individuals unfamiliar with enterprise-level security tools.
Users might also consider LastPass Authenticator, which is compatible with LastPass password manager, providing an integrated approach to security. It allows users to generate one-time passwords for their accounts while managing their credentials effectively. Nonetheless, the reliance on LastPass may deter users who prefer standalone solutions.
Lastly, FreeOTP serves as an open-source alternative. This app supports various services and offers a user-friendly experience without the need for account creation. However, its development seems less active, potentially raising concerns about long-term support.
Best Practices for Using Mobile Authentication Apps
As we transition to a mobile-only future for authentication, utilizing mobile authentication apps effectively is crucial to maintaining security. To begin with, it is essential to download authentication apps from trusted sources, such as the official app store of your device’s operating system. This preventive measure ensures that you are using a legitimate app, reducing the risk of malware or phishing attacks that can compromise your security.
Once the app is installed, setting it up properly is paramount. Users should enable biometric authentication, such as fingerprint or facial recognition, if available. This adds an additional layer of protection, making unauthorized access increasingly difficult. Furthermore, it is advisable to back up recovery codes generated by the app, as losing access to your mobile device can hinder your ability to retrieve important accounts.
Securing your mobile device is equally important. Employing a strong password or PIN, combined with data encryption, will protect your sensitive information from unauthorized access. Regular software updates are also crucial, as they often include security enhancements that safeguard against emerging threats. Additionally, avoid connecting to public Wi-Fi networks when managing sensitive accounts, as these can expose data to potential interception.
In the event of common issues with mobile two-factor authentication (2FA), such as not receiving codes or app malfunction, users should first check their device’s connection and ensure notifications are enabled. If problems persist, reinstalling the mobile authentication app or consulting the support section of the app’s website can provide guidance and solutions. Regularly reviewing security settings and practices is an effective strategy for maintaining robust security in an increasingly mobile-centric world.
Community Reactions and Feedback
The decision to discontinue the Authy desktop app has elicited a wide range of reactions from users across various platforms, including forums and social media. Many users expressed their disappointment and concern regarding the shift towards a solely mobile-based authentication method. The desktop app offered convenience for those who preferred managing their two-factor authentication (2FA) from a personal computer, particularly in work environments where mobile device usage may be restricted.
Several community members voiced their concerns about potential security implications of relying solely on mobile devices. Users pointed out that smartphones can be lost or stolen, and the idea of managing vital security tools on a single device presents a potential risk. Some users have also highlighted the challenges faced by those who frequently work on computers but may not have immediate access to their mobile devices for authentication purposes. This concern has resonate with professionals, particularly in fields where rapid access to verification codes is crucial.
In response to the discontinuation, the community has engaged in various discussions regarding alternative solutions. Some users have recommended enhancing the mobile app’s functionality to incorporate features that would help mitigate frustrations. Suggestions include the integration of desktop-like elements within the mobile application, thereby offering a user experience that aligns with what many have grown accustomed to on the desktop platform.
Despite the evident dissatisfaction, there are users who acknowledge the necessity for streamlined services that align with contemporary trends. These individuals understand the rationale behind focusing on mobile-first solutions and emphasize that mobile devices have become central to personal and organizational security. Overall, the community feedback represents a mix of frustration, concern, and adaptation to the evolving landscape of authentication tools.
Conclusion: The Future of Two-Factor Authentication
The discontinuation of the Authy desktop app marks a pivotal shift in the evolution of two-factor authentication (2FA). As organizations and individuals increasingly prioritize mobile devices for their security needs, this transition highlights the ongoing importance of mobile-centric authentication solutions. The decision to embrace a mobile-only future underscores a broader trend in cybersecurity, emphasizing convenience and accessibility alongside robust security measures.
In this mobile era, the reliance on smartphones for 2FA presents numerous advantages. Mobile devices offer advanced biometric authentication options, such as fingerprint and facial recognition technology, which enhance security by making unauthorized access significantly more difficult. Furthermore, the incorporation of push notifications simplifies the user experience, streamlining the authentication process. As security threats continue to evolve, these innovative approaches to two-factor authentication will be essential in upholding user data protection.
Looking ahead, the future of authentication technologies seems promising. We can anticipate the development of even more sophisticated solutions that combine various methods of verification, such as behavioral biometrics, to offer seamless yet secure user experiences. An increased focus on user education will also be critical as individuals navigate more complex security landscapes. Emerging trends in artificial intelligence and machine learning hold the potential to predict and mitigate security threats proactively, further enhancing the efficacy of authentication systems.
In summary, the move towards mobile-only 2FA not only aligns with technological advancements but also addresses the evolving nature of security needs today. As businesses and users adapt to this landscape, it is crucial to remain vigilant and proactive in utilizing these developments to safeguard digital identities effectively. The evolution of authentication technologies will continue to shape the way we interact with our digital environments, leading to a more secure future.
We share information about current trends and stories of people all around the world.